Tl;dr
In today’s edition of Cybersec Charcha, we’ll be exploring the growing role of Nation State Actors in cyberattacks, some important headlines from the past month in the cybersecurity space and some expert advice that we received on the last edition of Cybersec Charcha. Let’s dive right into it!
Nation State Actors - Who are they and what do they do?
A nation-state threat actor is a government sponsored group that forcefully targets and gains illicit access to the networks of other governments or to industry groups to steal, damage, and/or change information.
In the past there have been repeated instances of nation state actors using cyberattacks to further their respective agendas. The goal of these attacks can range from stealing intellectual property, attacks against corporations, and quite simply to steal money.
A 100% rise in significant nation state incidents
A research paper titled Nation States, Cyber Conflict and the Web of Profit, conducted by Dr. Mike McGuire, Senior Lecturer in Criminology at the University of Surrey, and sponsored by HP Inc. – highlights there has been a 100% rise in ‘significant’ nation state incidents between 2017-2020.
This study analysed over 200 cybersecurity incidents that could be attributed to nation state activity since 2009. It showed that some of the most common targets are the enterprise at 35%, followed by cyber defence at 25%, attacks on the media, government bodies and critical infrastructure at 14%, 12% and 10% respectively.
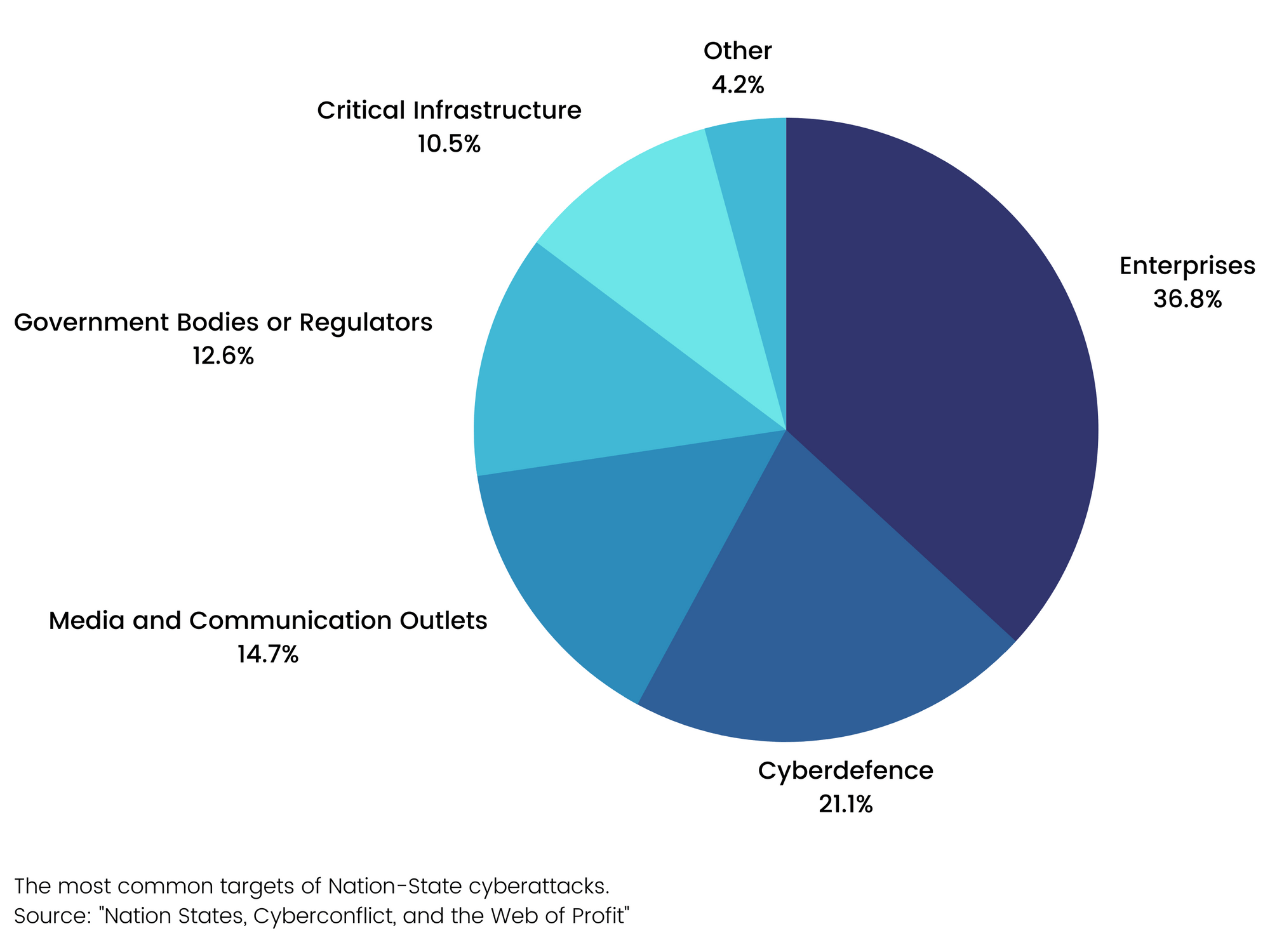
The study also drew from first hand intelligence gathering from informants across the dark web along with consultations with an expert panel of 50 leading practitioners in fields such as cybersecurity, intelligence, government, academia, and law enforcement. Some of the other key findings included:
- 75% of the expert panel opined that COVID-19 presented a ‘significant opportunity’ for nation states to exploit.
- ‘Supply chain’ attacks saw a rise of 78% in 2019; between 2017 and 2020 there were over 27 distinct supply chain attacks which could be associated with nation state actors. To understand what a Supply chain attack is, click here.
- There is also evidence that nation states are ‘stock-piling’ Zero Day vulnerabilities. The term “zero-day” refers to a newly discovered software vulnerability. Because the developer has just learned of the flaw, it also means an official patch or update to fix the issue hasn’t been released. So, “zero-day” refers to the fact that the developers have “zero days” to fix the problem that has just been exposed and perhaps already exploited by hackers. Read more about “zero days”, here.
- The “Web of Profit”: 65% of the expert panel believe nation states are making money from cybercrime, while 58% say it is becoming more common for nation states to recruit cybercriminals to conduct cyberattacks.
The study has some important findings and will help you understand the growing scale of nation state threat actors and their motivations behind these attacks. The research along with all their findings can be found here.
So, how can you prevent a breach?
- Cyberconflict Treaty: One of the things the study also looked into was the prospect of nations signing a “cyber-treaty”. 70% of the expert panel said it is necessary to create a cyberconflict treaty to de-escalate cyber-tensions and prevent nation states from being drawn into further acts of cyberconflict. However, only 15% believed that any such treaty will be signed in the next 5-10 years, and 37% said it’ll take anywhere around 10-20 years. A further 30% believed there is no prospect of any cyber-treaty within any timeframe. So maybe it’s best we don’t count on diplomacy to save the day anytime soon!
- Risk Management: Experts of cyber security suggest that a strong foundation of risk management, when applied correctly, can lessen the potential damage, simply by compartmentalizing sensitive data from non-sensitive.
- Tactical Approach: It is important to build sturdy and resilient systems along with multiple backups, which can easily be recovered after a cyber attack. The next step should be to ensure that the software is updated and patched.
- Educate! Educate! Educate!: Cybersecurity is not (just) a tech problem. Organizations need to focus on the people, and invest time and resources in training them on digital security practices. They need to be trained keeping in mind the kind of work they do within the organization and the sensitivity of the systems they have access to. Teach them about phishing scams, the importance of updating softwares, and inculcating habits of setting up 2 Factor authentication and using Password Managers.
In other news…
- False alarm!: On June 10th, a tweet started doing the rounds that data of 150 Million vaccinated people in India was leaked on the Dark Web. But within a few hours, independent security researchers and the Health Ministry confirmed that no such breach had occurred and our data was safe (for now).
- TechCrunch has published a really cool piece on how we can address the cybersecurity skills gap through neurodiversity! The article states, “There are many inherent traits in people with autism that are well suited for working in cybersecurity. For example, many people with autism are pattern thinkers and are highly detail-oriented. This allows someone in a threat-hunting position to find those subtle differences between malicious and nonmalicious code and catch the threats that automated tools might miss.” The article makes some really good points and I’d encourage you to dedicate some time and read it.
Some expert advice we received on the last edition of Cybersec Charcha…
The last edition of this newsletter focused on what ransomware attacks are. As a part of the post, we also mentioned a few things we can do to prevent ourselves from falling prey to these attacks. One of the tips I suggested is not clicking on links before verifying them. However, our community member Swapneel Patnekar wrote to us and pointed out a really important caveat here. Let’s take a 5 second test: Which amongst these is a malicious domain? https://twitter.com/NordVPN/status/1318888002123403267?s=20.
Well, in a case such as the one mentioned above, it’s next to impossible to verify what’s a malicious link and what isn’t. But thankfully for us, Swapneel also referred us to a different solution: A better way to counter the phishing problem - to the extent where a login is involved - is by using a password manager. Password managers are not just ideal to store and generate passwords but most of them also come with an “autofill” feature. If the user accesses a phishing domain of a service they regularly use (subject to a log-in), the autofill feature won’t work if the link doesn’t match! However, this doesn't mean we can drop our guard when clicking on unknown links, as the above mentioned solution will work only where a log-in is involved. In most other cases, we must continue to be diligent and avoid opening unknown links as much as possible.
Thanks to Swapneel and all our community members who regularly reach out to us with important feedback that helps us do our work better. Please continue to write out to us and tell us how we’re doing. As always, we aim to listen, learn and grow!
If you like the work IFF does, please consider becoming a member or making a one time donation. It’s your unending support and generosity that enables us to continue our work with autonomy!
